

Globally, a new cyberattack happens every 39 seconds.
Half of all UK businesses report having experienced a security attack in the past 12 months, and looking ahead to 2025, the annual global cost of cybercrime is projected to reach $10.5 trillion.
“I want to caution any business owner to take cyber-security extremely seriously” says Michael Dell, CEO of Dell. “For small, fast-growing businesses the risks are just as great, if not greater.”
One such risk is financial. For example, the average total cost per single data breach is estimated at $4.8 million. But it’s not just the financial consequences that pose a threat to businesses. The exposure of a businesses’ sensitive data and intellectual property can be even more damaging. Rebuilding lost data is costly, if not impossible, as is rebuilding company reputation and repairing the resulting lack of public trust. As Stéphane Nappo, GroupeSEB CISO puts it, “It takes 20 years to build a reputation and a few minutes of cyber-incident to ruin it.”
To mitigate these risks, firewalls have remained a consistent security practice since their development in the 1980s. 75% of UK businesses have adopted firewalls that either cover their entire network, or individual devices. The question is, which type of firewall is right for you?
This blog will cover how a firewall works, the differences between hardware and software firewalls, and the future of this type of security protection.
Table of contents
A firewall is a security system that filters incoming traffic to a device. It is configured to understand which traffic is safe and which traffic might pose a threat. The filtering is based on the packet data, such as source, destination and content. Consider a firewall as a data gatekeeper.
There are two main types of firewall:
A hardware (network) firewall
A software (OS) firewall
As the names suggest, a hardware firewall sits within the network and a software firewall is installed into the operating system (OS) of the device itself.
A hardware firewall is a physical device that sits between your private network and the public network (the internet). It checks all the traffic going in and out to make sure nothing malicious gets through.
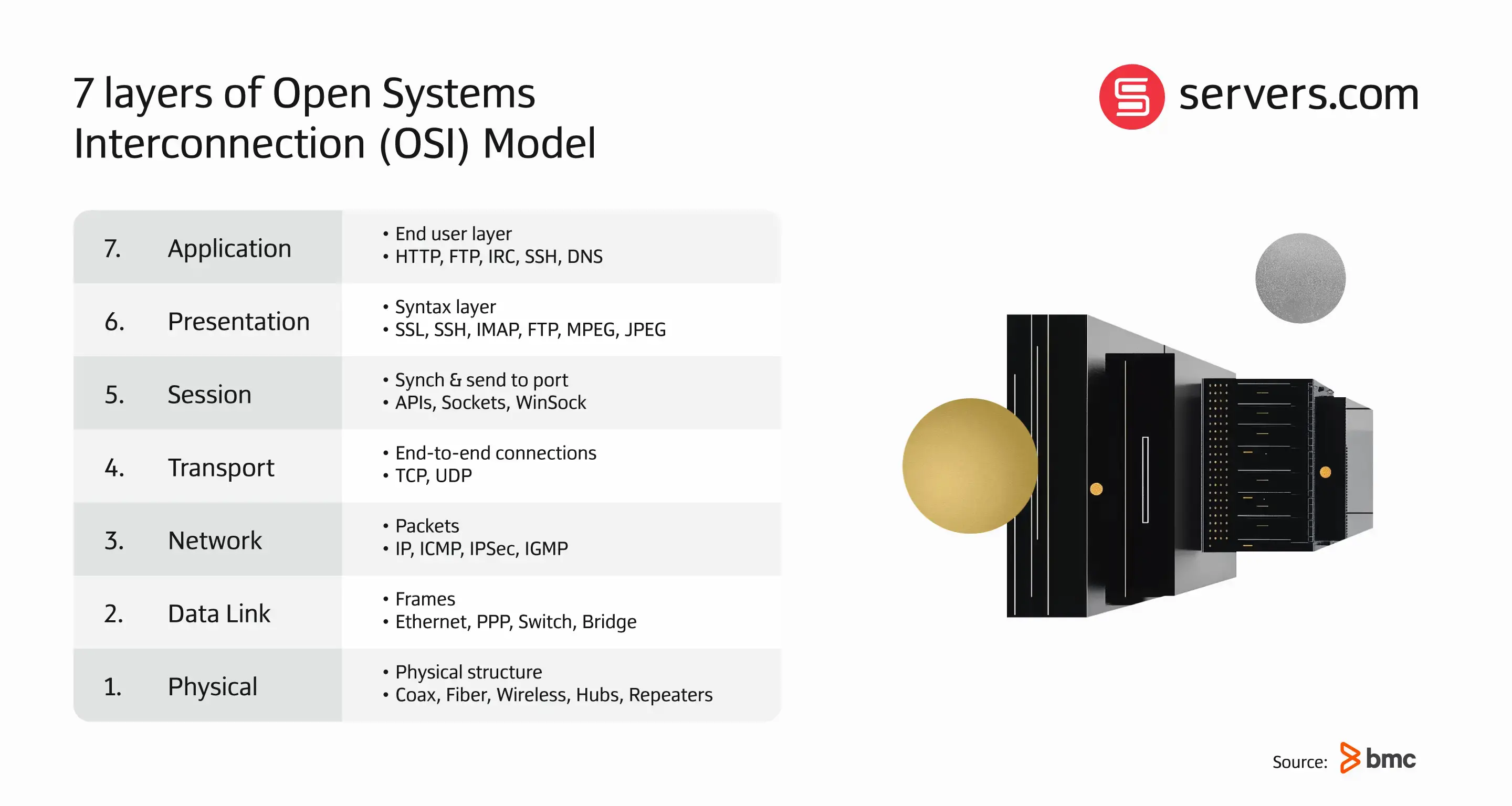
Hardware firewalls can be inserted on layers 3 (network) and 4 (transport) of the Open Systems Communication (OSI) Model and will protect every device that is connected to your network. Common examples include Cisco ASA and SonicWall Network Security Appliances.
A software firewall is an application that is installed directly onto the OS of your computer or server. Managed by the user or system administrator, software firewalls watch your network traffic and block anything suspicious. Unlike hardware firewalls, software firewalls protect the individual machine rather than the whole network.
Common examples include Windows Firewall, MacOS, and built-in firewalls on Linux.
Running a firewall on the network vs on the OS are two completely different methods of filtering incoming traffic. The best way to figure out which firewall is best for you is by answering the question: how many devices do I need to protect?
If you are responsible for multiple devices that all need to follow the same firewall configurations, a hardware firewall is the most efficient and secure option. As the data is scrutinized at the network level, every device on that network is under the same protection. And because a hardware firewall is separate from the devices it’s protecting, there’s no performance overhead.
This makes a hardware firewall ideal for:
Protecting an entire company’s network from outside threats
Implementing broad security policies that apply to everyone in an organisation
Managing traffic between different parts of your network (like internal and guest networks)
But be aware: you will need a team with expertise to set up, manage and manually update hardware firewalls. And if your firewall goes down without a redundancy plan, every device under that network will automatically lose their connection. Running two hardware firewalls in a redundant pair alleviates this risk of having your network entirely dependent on one firewall.
If you’re seeking protection for just a single device however, the costs, maintenance and expertise needed to run a hardware firewall is not generally worth it. This is when a software firewall may be the answer. Software firewalls are easy to set up, can be specific about which apps are allowed to connect, and are usually free since they’re built into the OS.
Software firewalls are ideal for:
Securing a single server or workstation
Adding an extra layer of security on top of a network firewall
Protecting laptops and mobile devices for remote work
However, malware can disable software firewalls, and because they are installed directly onto the device, they will use some of the machine’s resources, which may affect overall performance.
|
|
Hardware firewall |
Software firewall |
|
Level of protection |
Covers the entire network, not just one device |
Only protects the device it’s on, not the entire network |
|
Cost |
Can be expensive due to the hardware and set-up costs |
Is usually free as it’s built into the OS |
|
Compute |
Does not interfere with the performance of any device, as the hardware sits on the network |
As the software uses the machine’s resources, overall performance is affected |
|
Setup |
Will typically require a team of experts due to its complexity |
Very easy to set up on a device |
Cybersecurity is a constant arms race. Even though security tools are developed to mitigate against attacks, it doesn’t take long for new attack methods to emerge.
Next-generation firewalls (NGFWs) is the latest in firewall technology that is trying to tackle the problem. NGFWs have the most advanced firewall features; they don’t just filter traffic, they deep-packet inspect encrypted traffic, block intrusions, and integrate with threat intelligence feeds, so they are always up to date with the latest attacks.
NGFWs are installed onto the network as a more advanced hardware firewall, allowing packets to be analysed up to the 7th (application) layer of the OSI model – far deeper than a traditional firewall.
Whilst they are often more expensive than traditional hardware firewalls and can be more complex to set-up due to their advanced features, they offer the best overall firewall protection against cyber-attacks.
Traffic filtering analyzes each data packet and assesses it against the criteria of your pre-configured policy, so it knows whether to allow or block the traffic. These filters can range from limiting traffic from a user type or group, to specific IP addresses, protocols and port numbers.
If traffic filtering is like a security checkpoint at the entrance of a network, then access control is about deciding what can go where within that network. Through configuring privileges and understanding which roles have access to different parts of the network, everything else incoming or outgoing would be denied by default.
Often needed to follow security compliance regulation, the logging and monitoring of network behaviour ensures the early detection of a security incident, helping to minimize the impact of a breach. Logging also enables administrators to find patterns and analyze trends such as frequently accessed IPs and applications, so they can optimize security for those areas.
If a software firewall isn’t automatically installed onto the OS, independently sourcing a software firewall is as simple as downloading from a trusted provider.
On the other hand, a hardware firewall requires several stages with a team of experts, such as:
Assessing security needs and network mapping
Security policies and redundancy planning
Physical setup and configuration
Testing and validation
Ongoing monitoring, management and maintenance
If this process is beyond your resources but you’re still in need of a hardware firewall, infrastructure as a service (IaaS) may be of help. If you are partnered with a hosting provider for your servers, Firewall as a Service (FaaS) is an additional feature where the provider will manage and maintain the hardware firewalls for you. You will still be in control of all its configurations.
First and foremost, working backwards and adopting a ‘deny all’ policy – where all incoming and outgoing traffic is blocked by default – is the most secure method of provisioning a firewall.
By starting with a baseline of complete denial, you are eliminating any risk of illegitimate traffic right from the outset. With this foundation in place, you can then work backwards in opening the doors to the sources that you trust. This means outlining precise rules in your traffic filtering and access control.
But finishing the setup of your firewall doesn’t mean your work is done. Regular rule reviews make sure that the firewall keeps up to date with evolving business practices, such as any changes in network structure, new applications or retired services. Not responding to these changes can create vulnerabilities, giving opportunity for potential attackers to find the outdated points in your defence. These findings can inform new policies, ensuring the firewall develops at the same rate as the organisation. We recommend a review every few months.
The demand for cybersecurity has never been higher. In an age where data is our most valuable currency, it’s crucial that businesses protect themselves and their customers from potential threats.
Firewalls are a tried and tested security measure, allowing businesses to arm themselves with protection that can span either a network, or a singular device. Through NGFWs, network firewalls are continually developing and ensure a layer of defence against even the latest methods of attacks.

Nathan studied Creative Writing at Bath Spa University, including a six-month Erasmus scheme at Stockholm University in 2020. Outside of work, Nathan is both a film buff and car enthusiast.