How to replace password-based SSH authentication with key-based
To replace password-based SSH authentication with key-based, you need to set up key-based authentication first and disable password-based authentication afterward. Disabling password-based authentication before setting up key-based authentication may result in locking yourself out of SSH access.
Setting up key-based authentication
To set up key-based authentication, you will need a key pair (how to сreate one).
Add your public key to "~/.ssh/authorized_keys" as a new line using the "nano" text editor (how to install it):
nano ~/.ssh/authorized_keys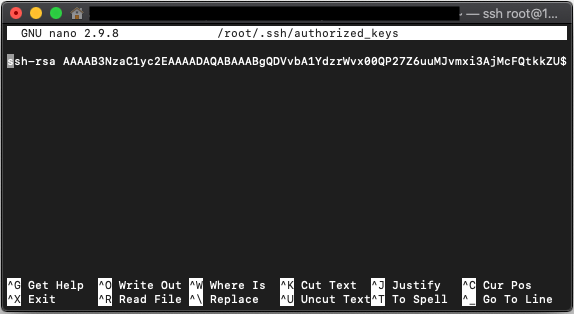
Verify that you can establish a new SSH connection to the server using your private key (assuming the private key is "~/.ssh/id_rsa"):
ssh root@host -i ~/.ssh/id_rsaDisabling key-based authentication
Open "/etc/ssh/sshd_config" for editing:
nano /etc/ssh/sshd_configFind and replace:
PasswordAuthentication yesWith:
PasswordAuthentication noVerify that there is only one uncommented "PasswordAuthentication" line in "sshd_config":
cat /etc/ssh/sshd_config | grep '^[ \t]*PasswordAuthentication'Restart the "sshd" service ("systemd" service manager is the default for both, Debian/Ubuntu and RHEL/AlmaLinux machines):
systemctl restart sshd